

The Blockchain: Ending Data Hacks
Remember when we were scared to buy things online? It wasn’t all that long ago when we swiped plastic cards in person for everything we bought, Black Friday meant toe-to-toe battles with every other holiday shopper in the mall, and the thought of entering your personal financial info into a website to buy something terrified many shoppers.
As a nosy prepubescent, I eavesdropped on these ‘adult’ conversations about internet purchasing on our landline between my parents and relatives or family friends as I eagerly awaited my turn to warp our home phone into a glorious portal transporting me to the land of America Online and A.I.M. Those conversations generally centered on doubt and fear as to whether it was safe and/or reliable to buy stuff over the web. It wasn’t just my parents. In 2002, online commerce accounted for just 1.6% of total retail sales in the U.S. Fourteen years later, consumers in the U.S. spent more than $258 billion online and 80% of the U.S. population has E-bought at least once.
Times have changed to be sure. Although it may now turn out that the safety and security concerns many Web 1.0 consumers felt weren’t as readily dismissed as most AIM screennames from that time (i.e. cybernero or dimtim123). Those internet commerce websites, not to mention social media platforms, online banking accounts, and any other digital destination where we’ve left our identities, personal information and financial access, aren’t foolproof vaults for storing our sensitive data. Whether outspoken or tacit, all parties have acknowledged foreign hacking during the 2016 presidential election. That breach alone demonstrates the premium efficacy of targeted hacking at the high stakes geo-political level. Yet, since 2007 hacks and leaks have exposed, compromised or stolen hundreds of billions of online accounts that belong to regular people, Yahoo, Dropbox, Adobe, Chase, LinkedIn, Ebay, Slack are all listed here.
The point is not to cast endless blame on the companies breached.
The proliferation of sensitive data stored online combined with the ever-increasing total number of individuals online have produced sprawling, vulnerable databases that we expect to perform in exact accordance with the Terms of Service box we check before confirming a payment or signing into an account. Code is permeable and we’ve dumped entirely too much of our sensitive data on the web for those platforms and institutions to keep safe and sound from bad actors.
I’ve drawn out the preamble here to highlight a circuitous path of online progress. In doubling back to some of the earliest fears of the World Wide Web and demonstrating that some of them were and still are valid, we’ve arrived at a jump off point for a new technological revolution. When we started buying things online and storing our information and identities online, we believed that the merchants and firms who had kept such data safe in the physical world could do so in the digital world just as well. As packages arrived on time and payments went to the right places, we may have begun to believe that a password-protected or 3rd party encrypted online checking account was as safe as a bank vault. But it isn’t. Maybe there isn’t a single entity anywhere that should be expected to perpetually protect the endless mass of sensitive data we produce in leaving our identities all over the place online.
To me, this problem presents an amazing opportunity for widespread adoption of blockchain technology as a solution for all involved individuals and firms. If an explanation or refresher is needed on what that technology is read The Blockchain Application Stack by Joel Monegro or Don Tapscott’s Blockchain Revolution.
In the context of this post on user-level data security, here’s the bitcoin blockchain solution in Before and After diagrams below:
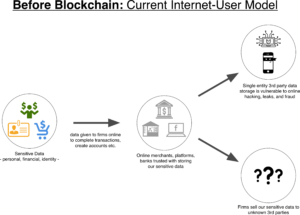
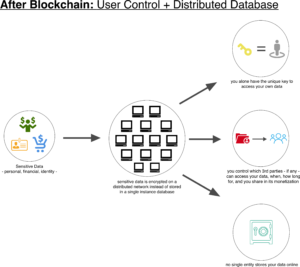
In the second diagram, the bitcoin blockchain infrastructure eliminates the need for any single entity to keep and store your sensitive data (including you). Any business or platform that integrate open-source blockchain APIs for any account verification, access or transaction will provide an innovative level of data security as diagrammed.
Reimagining an exchange fundamental to the known internet is necessary if not inevitable. To date, this exchange has been between internet users and internet businesses, with users providing their data – usage, personal, financial, demographic – in return for information and services. In many cases, users have gladly surrendered personal data for answers, for efficiencies, for stuff, and for access. This accepted internet-user model allowed several companies to achieve profound levels of product efficacy and total enterprise value due to an ever-expanding stockpile of user data they’ve kept and built around. Google, Amazon, Facebook, Uber and Netflix are a few examples. To redirect the current flow of online user data means redefining what is considered valuable on the internet for every entity from the tech titans just referenced to newly founded startups. Network effects and data moats, two tenants underlying some of the most significant web products and overall internet activity to date, are in many ways undone when the blockchain empowers users to keep and control their data.
If that change sounds daunting, that’s because it will be. But add up all the zeros in that awesome data breach visualization from the site Information Is Beautiful and you see how vulnerable we are right now. Which brings me back to the original Web 1.0 concerns about commerce and identity online:
Will it work? Yes indeed.
Can my credit card number get stolen? Most definitely.
Am I being tracked? 100%.
Do they see my profile activity and password? Oh yes.
Is it safe? Well, we thought so…
If the blockchain is a technology that can actually fix these problems, why don’t we all start using it? Of course, many millions of users don’t mind the traditional internet-user model and see so much value and ease of use on the web today that they consider it a fair trade. There are likely many more millions of users who would shift to a blockchain model and yet relinquish their encrypted keys to a blockchain entity to manage and secure. The core process of transaction verification via the bitcoin blockchain needs to continue to progress to a faster and cheaper end product. And internet-wide adoption and integration will require both continued education across the board and tremendous buy-in from today’s large internet companies.
The question with the blockchain has usually been: where’s the tipping point? In theory, its democratic and universally honest; in explanation, its extremely complex technology to understand; in execution, it requires a massive swing up the adoption curve to meaningfully deliver. If I could plot this timeline exactly, I already would have. But if the infrastructure of today’s internet is increasingly at odds with users’ rabid, data-heavy activity and the high-margin business models making internet companies rich, then more and more data breaches could eventually topple the whole system. So, here’s one vote for the blockchain coming to save the day.





